Is your website truly secure?
In the digital world, where user data is at the heart of every online interaction, front-end security has become a critical concern for businesses.
As a website developer or entrepreneur, you are responsible for protecting user data and ensuring your digital platform’s integrity.
But how can you effectively shield your website and its users from the ever-evolving threats that loom in cyberspace?
We’ve compiled this post to let you know about the importance of front-end security and its role in protecting user data.
From understanding the top secure front-end development tech stack to implementing effective security testing strategies, we will provide actionable insights to fortify your applications.
Table of Contents
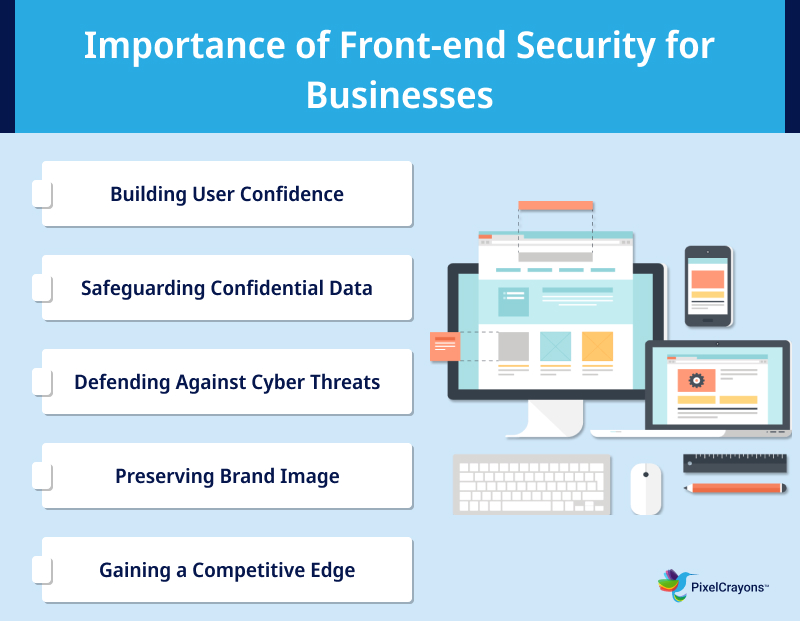
Why Do Businesses Need Front-end Security?
According to Charged Retail, 80% of consumers are concerned about the security of their personal data when using online services. In an era of increasing cyber threats, businesses must prioritize front-end security to protect user data and prevent vulnerabilities.
Here are key reasons why front-end security is crucial for businesses:
Safeguard User Trust
By implementing robust front-end security measures, businesses demonstrate their commitment to protecting user data, enhancing trust, and building long-term customer relationships.
Protect Sensitive Information
Front-end security ensures the confidentiality of sensitive information, such as personal details, financial data, and login credentials, safeguarding it from unauthorized access or breaches.
Prevent Cyber Attacks
Effective front-end security practices, such as input validation, output encoding, and protection against cross-site scripting (XSS) attacks, help prevent malicious actors from exploiting vulnerabilities and compromising user accounts or systems.
Ensure Compliance With Regulations
Businesses must comply with data protection and privacy laws in an increasingly regulated environment. Implementing front-end security measures helps meet these compliance requirements and avoid potential financial and legal consequences.
Maintain Brand Reputation
A security breach can severely damage a business’s reputation. By prioritizing front-end security, organizations protect their brand image and demonstrate their commitment to user privacy and data protection.
Stay Ahead of Competitors
Businesses that prioritize front-end security gain a competitive advantage. Customers are more likely to choose companies that prioritize their security and privacy, boosting customer acquisition and retention.
Get in Touch with PixelCrayons Experts Today.
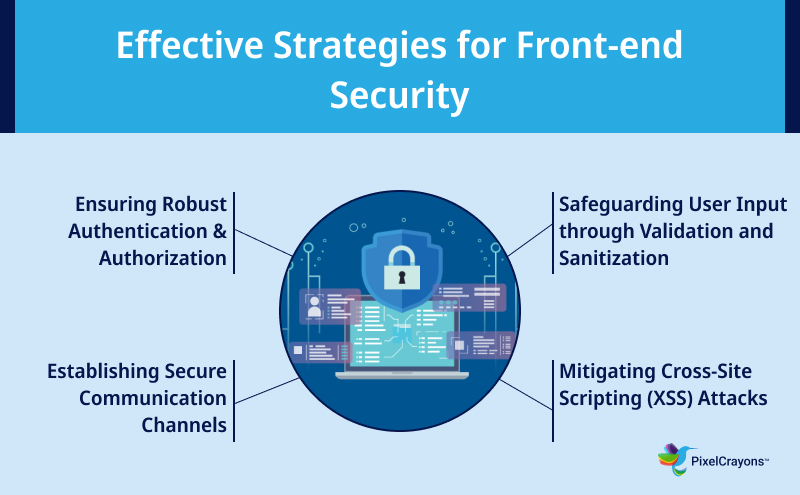
Best Practices for Front-end Security
Ensuring robust front-end security is essential for safeguarding user data and preventing vulnerabilities. This section explores effective strategies and best practices to strengthen your front-end web security defenses.
Secure Authentication & Authorization
Did you know? Weak or compromised passwords are responsible for 81% of hacking-related breaches.
To mitigate this risk, it is crucial to enforce strong password policies and implement multi-factor authentication (MFA) methods.
It ensures an added layer of protection by requiring users to provide additional verification, like a fingerprint or SMS code.
Additionally, proper user role management and access control measures should be in place to limit user privileges and prevent unauthorized access to sensitive areas of the application.
- Utilize strong password policies and encourage users to choose unique, complex passwords.
- Implement multi-factor authentication (MFA) methods to enhance user authentication.
- Employ role-based access control (RBAC) to ensure users have appropriate permissions.
Input Validation & Sanitization
Did you know? Injection attacks, such as cross-site scripting (XSS), account for 40% of reported vulnerabilities.
To prevent these attacks, validating and sanitizing user inputs is vital. Implement client-side and server-side validation techniques to ensure that only expected and safe inputs are accepted.
It helps mitigate the risk of malicious code being injected into the application.
- Validate and sanitize user inputs on both the client and server sides.
- Use input validation libraries and frameworks to automate the process.
- Employ strict content security policies (CSP) to restrict the execution of untrusted scripts.
Secure Communication
Data transmitted over insecure channels can be intercepted and manipulated by attackers. To protect sensitive information, it is essential to use the HTTPS protocol, which encrypts data in transit.
Adopting secure communication protocols and APIs further enhances the security of data exchanged between the client and server.
- Implement HTTPS to encrypt data transmitted between the client and server.
- Use secure communication protocols like TLS to ensure data integrity and confidentiality.
- Validate TLS/SSL certificates to prevent man-in-the-middle attacks.
Cross-site Scripting (XSS) Prevention
These attacks allow hackers to inject malicious scripts into web pages, compromising user data and enabling further attacks.
To prevent XSS attacks, it is crucial to implement input/output encoding techniques and enforce strict content security policies.
- Apply input/output encoding techniques to sanitize user inputs and prevent script injection.
- Implement strict content security policies (CSP) to restrict the execution of untrusted scripts.
- Regularly update and patch frameworks and libraries to mitigate known vulnerabilities.
Following the above practices, businesses can significantly enhance front-end security and protect user data from potential vulnerabilities and threats.
It is essential to stay proactive and implement a comprehensive security strategy to ensure a safe and secure user experience.
Regular Security Testing & Auditing
Regular security testing and auditing are crucial to ensure the robustness and resilience of front-end applications.
Businesses can proactively identify and address vulnerabilities by conducting comprehensive evaluations, safeguarding user data, and preventing potential breaches.
Importance of conducting regular security testing and audits:
- Identifies and mitigates potential vulnerabilities before they can be exploited.
- Ensures compliance with industry standards and regulations.
- Enhances the overall security posture of front-end applications.
- Provides reassurance to users and builds trust in the brand.
- Helps in identifying weaknesses in coding practices or configurations.
- Enables proactive identification and mitigation of emerging threats.
Utilization of automated tools and manual inspections:
- Automated tools like OWASP ZAP and Burp Suite can perform scans and identify common vulnerabilities such as XSS and SQL injection.
- Manual inspections by security professionals can uncover complex vulnerabilities that automated tools might miss.
- A combination of automated tools and manual inspections provides a comprehensive assessment.
Collaboration with security professionals:
- Engaging security professionals helps in obtaining external expertise and fresh perspectives.
- Security professionals can conduct in-depth penetration testing, code reviews, and vulnerability assessments.
- Their insights and recommendations contribute to strengthening the overall security framework.
By incorporating regular security testing and auditing into their processes, businesses can proactively identify and mitigate vulnerabilities. This will ensure the ongoing protection of user data.
Automated tools and collaboration with security professionals further enhance the effectiveness and comprehensiveness of these evaluations. This enables businesses to stay ahead of emerging threats and maintain a secure front-end environment.
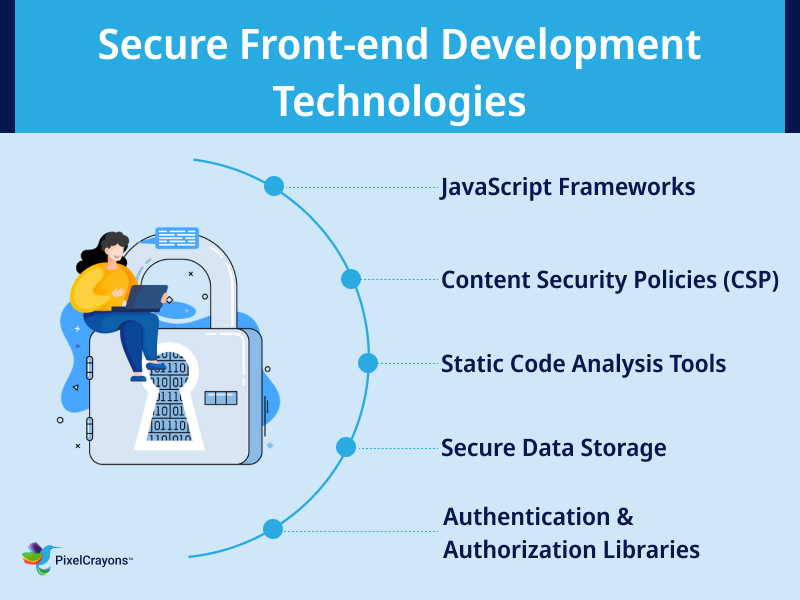
Top Secure Front-end Development Tech-Stack
When developing secure front-end applications, choosing the right tech stack is crucial. By leveraging cutting-edge tools and technologies, businesses can strengthen their front-end security and protect user data from potential front-end security vulnerabilities.
Here are some of the top secure front-end development tech-stack options to consider:
JavaScript Frameworks
Popular frameworks like React, Angular, and Vue.js provide robust security features, such as built-in cross-site scripting (XSS) protection, data sanitization, and content security policies (CSP). These frameworks offer a solid foundation for secure front-end development.
Content Security Policies (CSP)
Implementing CSP allows businesses to define and enforce security policies, mitigating the risk of cross-site scripting attacks. It helps control the resources loaded by a website and restricts the execution of potentially malicious scripts.
Static Code Analysis Tools
Utilizing tools like ESLint, JSLint, or JSHint enables developers to identify and fix potential security vulnerabilities during the coding phase. These tools provide real-time feedback on coding errors, insecure practices, and potential code injections.
Authentication & Authorization Libraries
Implementing secure authentication and authorization mechanisms is essential for front-end security. Libraries like JSON Web Tokens (JWT), Passport.js, and OAuth help ensure secure user authentication and restrict unauthorized access.
Secure Data Storage
Leveraging secure local storage mechanisms, such as Web Storage API and IndexedDB, helps protect sensitive user data from unauthorized access or tampering.
Why PixelCrayons for Secure Front-end Development?
At PixelCrayons, we understand the criticality of secure front-end development and prioritize it in every project we undertake.
With our expertise in cutting-edge front-end technologies and a strong focus on security, we ensure that your applications are robust, resilient, and protected against potential vulnerabilities.
Here’s how PixelCrayons provides secure front-end development:
Experienced Development Team
Our team of skilled front-end developers has extensive experience in building secure applications. They follow best practices and coding standards and adhere to industry security guidelines to minimize the risk of vulnerabilities.
Secure Coding Practices
We implement secure coding practices, such as input validation, output encoding, and proper handling of user input, to prevent common security vulnerabilities like Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF).
Technologies & Libraries
We leverage secure front-end frameworks and libraries like React, HTML, PWA, Chrome Dev Tools, jQuery, Angular, and Vue.js. These frameworks have built-in security features, regular updates, and community support, ensuring a strong foundation for secure application development.
Third-Party Integrations
When integrating third-party services, we carefully evaluate their security practices and ensure they align with our security standards. We conduct thorough security assessments and validations to minimize the risks associated with third-party dependencies.
Security Testing
We perform comprehensive security testing, including penetration and vulnerability assessments, to identify and address potential security gaps.
By conducting regular security audits, we can proactively address vulnerabilities and mitigate risks.
Some of the successful front-end development projects we’ve delivered so far are:
So, if you’re looking to expand your team and enhance your web development capabilities, it’s worth considering the option to hire front-end developers from us.
Final Call
In an era of rampant data breaches and cyber threats, prioritizing front-end security is more critical than ever. By implementing robust security measures, businesses can safeguard user data, prevent vulnerabilities, and maintain the trust of their customers.
From employing secure coding practices to encryption techniques, businesses must adopt a proactive approach to front-end web security. Remember, protecting user data is not just a legal and ethical responsibility but a crucial aspect of building a strong brand reputation.
So, invest in reputable front-end development services to build a secure website, stay updated with the latest threats, and ensure a secure digital experience for your users.
Together, we can build a safer online environment.
Get in touch with PixelCrayons professionals for all your project needs.
Frequently Asked Questions
1. What is front-end security?
Ans: Front-end security refers to the measures and practices implemented to protect a software application or website’s user interface and client-side components from potential threats and vulnerabilities. It involves safeguarding user data, preventing unauthorized access, and ensuring the integrity and confidentiality of the front-end components.
2. What are the front-end and back-end in security?
Ans: In security, the front-end and back-end refer to different layers of a software system. Front-end development security focuses on securing user-facing components, such as the user interface, client-side scripts, and user interactions. Back-end security, on the other hand, pertains to securing the server-side components, databases, APIs, and the underlying infrastructure of the application or website.
3. What is front-end risk?
Ans: Front-end risk refers to potential threats and vulnerabilities in a software application or website’s user interface and client-side components. These risks can include security vulnerabilities, data breaches, unauthorized access, cross-site scripting (XSS) attacks, and other malicious activities targeting the front-end components.
4. What are front-end security best practices?
Ans: Front-end security best practices include:
- Implementing secure coding practices to prevent common vulnerabilities, such as input validation and output encoding.
- Enforcing strong authentication and authorization mechanisms to control user access.
- Regularly updating and patching front-end frameworks, libraries, and dependencies.
- Implementing HTTPS encryption to secure data transmission between the client and server.
- Implementing content security policies (CSP) to mitigate cross-site scripting (XSS) attacks.
- Conducting regular security audits and vulnerability assessments to identify and address any potential weaknesses.
- Providing user education and awareness about security practices, such as avoiding suspicious links or downloads. and using strong passwords.
Make sure to follow the comprehensive front-end security checklist to ensure that your website or application is protected against potential threats and vulnerabilities.